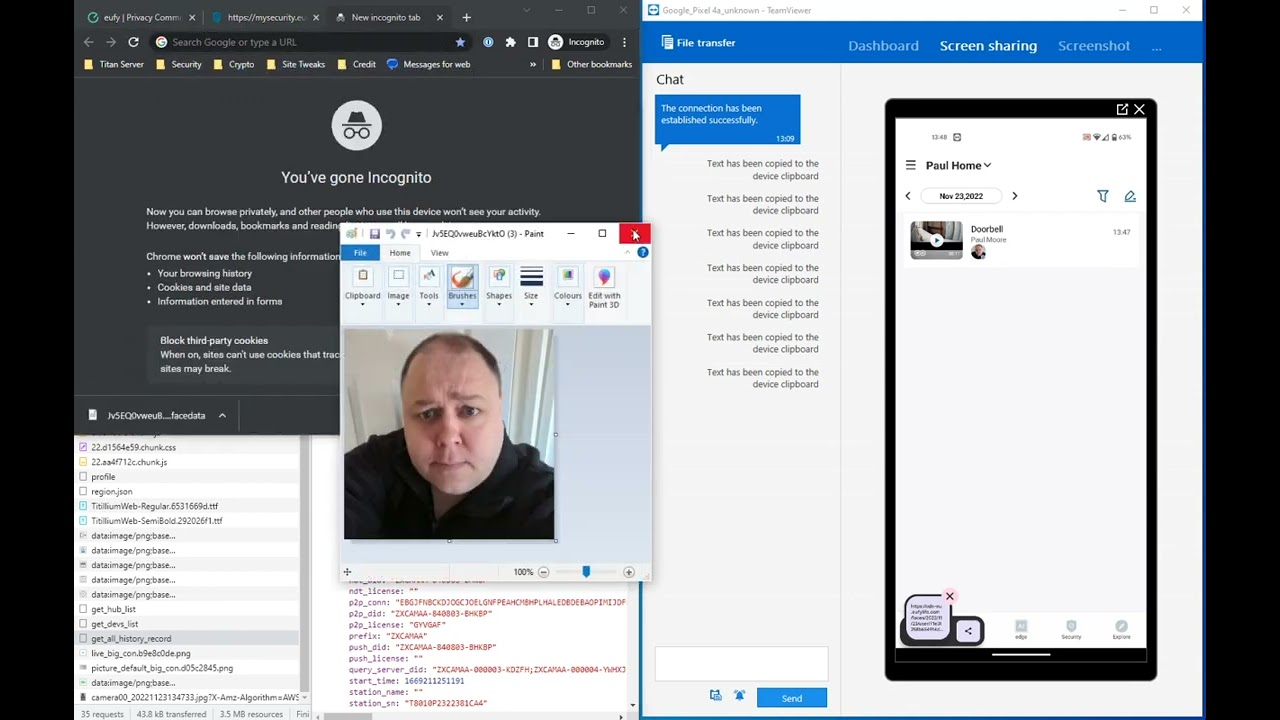
I’ve seen this doorbell discussed here so I thought some of you might be interested in this. It looks like “local-only” Eufy doorbells are happily streaming everything to the cloud.
Interesting. It looks like Eufy is providing a connection from the doorbell to his android phone. And that the doorbell is uploading a thumbnail to Eufy which then does its magic and forwards the info and thumbnail to the users phone.
With the exception of the user id (did he say was the same on two accounts?) everything seems reasonable to me. I wouldn’t expect a $200 device to be capable of doing face_id or being remotely controlled directly from a users phone. It appears that he is bothered by a thumbnail being stored in his user account on Eufy’s server.
again, I am not referring specifically to Eufy products, but a general discussion on the background of a lot of IOT manufacturers are not that transparent to us. See a related post here.
some more news about Eufy can be found here. Also there is a similar discussion here. In Australia, there was an incident of security breach, details here
A wikipedia page of Anker can be found here. Personally, I have no issue using Anker charger, etc. However, I am extremely cautious on choosing IOT and home network , automation devices, do not want to have a trojan horse within my own home network
It seems to get worse:
This is really a nothing-burger because you have three options when using RTSP streams: basic auth:
- Digest
- Basic
- Disable
the first two allow you to set a username and password on the stream.
The RTSP stream option is usually used with Synology Surveillance Station. And it is a live video stream, of course you can view them in VLC. It is up to the user to know the risks, and, if the user is enabling RTSP in the first place, which is off by default, then I think they already know what the risks are.
I’m curious why you have linked the Anker Wikipedia page when you are saying you’re generalizing your issue with IOT.
because Anker owns Eufy
An other article about the issue
The Verge has also corroborated the remote viewing exploit:
I had some friends that wanted a camera to watch a litter of puppies that they had. They set up the camera, and they wanted to be able to check in remotely. If I recall correctly, it was possible to do, but there wasn’t a way to password-protect the stream. I explained that we could totally set up the camera the way they wanted, but that they would effectively be allowing anybody with the correct web address to watch the stream.
The thought had never occurred to them. Why would somebody else on the Internet be able to watch their camera?
That’s the issue. Bad end-user education about risks of turning these options on.
I agree that there needs to be education for users about turning these features on. Rob from The Hookup, one of my favorite smart home/DIY electronics channels has more on this.
Rob’s explanation sounds reasonable and I’ll withhold my judgement until I hear “the rest of the story”.
I read about studies that say Americans, on the average, are caught by a security camera around 250 times a month. I wonder if that includes the millions of Ring Doorbells that have been sold in recent years?
Yes, and it is not a new problem!
There are myriades of IoT-Devices, Cameras, Door-Looks and what ever else, without a secure configuration, and a lot even without the possibility even for “advanced” Users, to get those devices “secure” to some level, as there are no possibilities to set a (own) password.
There are plannings now in Germany (Europe?) to set up a mandatory education plan for middle schools, to provide the pupil with at least a basic knowledge about those technologies, the risks of social media and so on.
Definitely. I have a Ring Gen 2 Alarm System and with the Ring app your neighbors can upload clips of “crimes” they’ve caught on their Ring doorbell cameras. Do we know what Amazon is doing with those clips? I don’t know but if users rely on Ring’s cloud storage to keep access to their clips for 60 days, the same thing is possible here.
So, they just make it official now, that they are spying their customer…
They’re definitely sharing them with local law enforcement. This we know. And while I agree that the hysteria was a bit overblown, this was definitely an issue and Euffy willingly misled their customers. Anyone smart enough to design a system that leverages the cloud in this way knows their claims about encryption and privacy are misleading at best.
Is anyone aware if this is the case using the cameras through Homekit or just the app?
It is the case, as long as there is a/their cloud service involved.